Handling sensitive data, staying compliant, and maintaining robust security measures are paramount considerations for a payment gateway in the digital age. The landscape of global commerce has been transformed by technological advancements, offering new opportunities for businesses and consumers alike.
However, these same advancements have also empowered cybercriminals with sophisticated methods to exploit vulnerabilities, targeting both merchants and their customers. Against this backdrop, it is essential for payment gateways to adopt comprehensive security practices to safeguard financial transactions and personal information.
Merchants, therefore, need to be well-informed about the security measures employed by payment gateways to make the best choice for their business. This article will explore the top 10 security measures that a payment gateway use to ensure a safe and secure transaction environment.
Table of Contents
ToggleWhat are Payment Gateways?
Payment gateways are critical cloud-based software solutions that serve as the intermediary between merchants and their customers during financial transactions. When a customer makes a purchase, be it through a physical Point Of Sale (POS) system in-store or via an online shopping platform, the payment gateway comes into play. A payment gateway is responsible for securely reading and transferring payment information from the customer’s end to the merchant’s bank account, typically processing this data in just a matter of seconds.
Beyond facilitating a seamless payment experience, it’s of utmost importance for fintech developers to focus on the security aspect of their payment gateways. This involves implementing measures that adhere to established industry standards, thereby ensuring that every transaction carried out is not only smooth but also highly secure against potential cyber threats.
How Do Payment Gateways Work?
Understanding the mechanics behind payment gateways elucidates their crucial role in the transaction process. Essentially, they ensure that the transfer of funds from a customer to a merchant is executed smoothly and securely. This process involves several critical steps, each designed to verify, encrypt, and also approve financial data to safeguard the integrity of the transaction.
Initiation by the Customer
The transaction begins when the customer initiates the purchase by filling in their card details on a website, tapping their card or mobile wallet on a card reader, and then confirming the purchase. The customer’s act of entering their payment information and confirming the purchase triggers the payment gateway to prepare for transaction processing.
Verification and Funds Check by the Payment Gateway
Once initiated, the payment gateway verifies the card details with the issuing bank and checks for sufficient funds in the customer’s account. This involves a security check to ensure the card has not been reported lost or stolen and that the transaction does not raise any red flags for fraudulent activity.
Encryption and Submission
The payment gateway encrypts the transaction details and submits them to the card network (Visa, MasterCard, etc.) involved in the transaction. Encryption is a critical security step that protects the customer’s financial data from potential cyber threats during transmission to the card schemes.
Card Scheme Approval
The card scheme reviews the transaction details sent by the payment gateway, and either approves or denies the transaction. This step involves another layer of fraud prevention checks by the card scheme to ensure the transaction’s legitimacy.
Transfer to Merchant’s Bank
Upon approval by the card scheme, the payment gateway forwards the transaction details to the merchant’s bank account. This step signifies that the transaction has passed all necessary checks and is considered legitimate and secure.
Finalization and Funds Transfer
The payment gateway sends the encrypted financial information to the acquiring bank, which then moves the funds from the customer’s account to the merchant’s account, completing the transaction. This final step marks the successful completion of the payment process, with funds securely transferred to the merchant and both parties notified of the concluded transaction.
Why are Payment Gateways Important?
Payment gateways play a pivotal role in the modern digital marketplace, primarily by acting as a bulwark against the escalating threats of financial fraud. In an age where the incidences of fraud seem omnipresent—from phishing schemes infiltrating our inboxes to banks meticulously verifying unexpected spending patterns—the need for robust defense mechanisms against these menaces has never been more critical.
With the digital domain expanding, opportunistic fraudsters find increasingly sophisticated means to exploit both customers and merchants, presenting a significant concern. European retail webshops, for instance, confront an average of 206,000 fraudulent attempts each month, highlighting the sheer scale and evolving nature of the challenge.
Fortunately, payment gateways are at the forefront of combating this issue, leveraging cutting-edge financial fraud detection technologies that employ artificial intelligence and machine learning. These systems are designed to monitor transactions meticulously, detect fraudulent activities in real-time, and also identify unusual behavior patterns that may indicate misconduct.
This ongoing technological evolution in e-commerce fraud detection underscores the necessity for merchants to invest in advanced systems that enhance the capability to detect and mitigate fraudulent transactions effectively. Essentially, choosing a payment gateway equipped with powerful fraud detection and prevention tools is the first crucial step for merchants aiming to safeguard their operations and provide a secure transaction environment for their customers.
Top 10 Payment Gateway Security Measures
In an era where digital payments are the norm, ensuring the security of these transactions is paramount for businesses and consumers alike. The measures taken to protect these payments are diverse, ranging from compliance with global standards to the deployment of sophisticated encryption technologies. The following security measures are critical for any payment gateway to maintain the trust and safety of its users.
PCI DSS Compliance
Compliance with the Payment Card Industry Data Security Standard (PCI DSS) is crucial for any payment gateway. This global standard ensures that all entities handling credit card information maintain a secure environment to protect sensitive data. It involves implementing security measures like maintaining a firewall, encrypting data transmissions, conducting regular security system tests, and establishing access control measures to safeguard against potential breaches and cyber threats. Failure to comply with PCI DSS requirements can result in hefty fines, reputational damage, and loss of customer trust. It is paramount for businesses to prioritize PCI DSS compliance to uphold data security and maintain trust with customers.
Security Socket Layer (SSL)
The use of Security Socket Layer (SSL) technology is fundamental for establishing a secure connection between a web server and a browser. This protocol ensures that all data passed between the web server and browsers remain private and integral, safeguarding against eavesdropping, tampering, or message forgery. Implementing SSL certificates also verifies the authenticity of websites, encrypts sensitive information, and boosts trust among users, enhancing overall cybersecurity and protecting against various cyber threats.
Data Encryption
Data encryption is a vital technique that converts data into a coded format, accessible only to individuals possessing the corresponding key or password. This security measure is commonly utilized by payment gateways to safeguard confidential details such as credit card numbers during transactions. By employing data encryption, sensitive information remains unreadable and secure, even if intercepted by unauthorized parties, ensuring the integrity of digital transactions.
Regular Security Audits
Conducting regular security audits is crucial to identify vulnerabilities and ensure that all security measures are functioning as intended. These audits can also help keep the payment gateway compliant with evolving security standards and regulations. By proactively addressing potential security risks, businesses can safeguard sensitive data, protect customer privacy, and maintain trust in their services.
Tokenization
Tokenization is a vital security measure that replaces sensitive data with unique identification symbols. These symbols maintain all essential information while safeguarding against security breaches. In payment processing, tokenization plays a crucial role in protecting card and transaction details. By substituting them with randomly generated numbers or tokens, any compromised data becomes useless to potential threats, ensuring the safety of financial transactions.
Secure Electronic Transaction (SET)
Secure Electronic Transaction (SET) is a robust system developed by Visa and MasterCard in the 1990s to enhance the security of online credit card transactions. It utilizes digital certificates to ensure the confidentiality of payment data and personal information. Additionally, SET offers message integrity verification, assuring that transactions remain unchanged during transmission. Furthermore, the system authenticates both the merchant and the buyer, creating a secure environment for electronic commerce.
Multi-factor Authentication
Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide two or more verification factors to gain access to a resource, such as an account or database. This can significantly reduce the risk of unauthorized access. Common verification factors include:
- Something you know (like a password).
- Something you have (like a mobile device).
- Something you are (like a fingerprint).
By combining these factors, MFA enhances security measures and protects sensitive information from potential breaches.
3D Secure 2.0
3D Secure 2.0 is an updated version of the security protocol designed to be more mobile-friendly and reduce the friction in the user experience during authentication. It adds a layer of security for online credit and debit card transactions by requiring the cardholder to complete an additional verification step with the card issuer. This updated protocol aims to enhance the security measures in e-commerce transactions, providing increased protection against fraudulent activities and enhancing user trust in online payments.
Fraud Monitoring Systems
Advanced fraud monitoring systems leverage artificial intelligence and machine learning to analyze transaction patterns in real time and flag suspicious activities. By continuously evolving and learning from new data, these systems can adapt to emerging fraud tactics, enhancing their ability to detect and prevent fraudulent transactions effectively. This proactive approach not only safeguards merchants and customers from financial loss but also helps maintain trust and security in the digital ecosystem.
Employee Training
Employee training is a critical security measure to ensure that those handling payment processing are aware of the potential risks and best practices for maintaining security. Regular training sessions can help prevent human error, which is a common cause of data breaches. By providing continuous education and simulated phishing exercises, employees can sharpen their awareness and responses to evolving cyber threats, ultimately fortifying the organization’s defense against data breaches.
Frequently Asked Questions (FAQs)
Q1: What is the difference between SSL and TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are both protocols designed for securing communications over a network. While SSL is the older of the two, TLS is its successor and offers more robust security features. In practice, TLS has largely replaced SSL; however, the term “SSL” is still commonly used to refer to secure connections.
Q2: How often should security audits be conducted for a payment gateway?
Security audits should be conducted on a regular basis, at least annually, or whenever significant changes are made to the system. This ensures that new vulnerabilities are identified and addressed promptly to maintain a high level of security.
Q3: Can tokenization eliminate payment fraud?
While tokenization significantly reduces the risk of payment fraud by making the intercepted data useless to attackers, it cannot completely eliminate the risk. Combining tokenization with other security measures like SSL, MFA, and fraud monitoring systems provides stronger protection against payment fraud.
Q4: How does 3D Secure 2.0 improve the checkout experience?
3D Secure 2.0 improves the checkout experience by making the authentication process more seamless, especially on mobile devices. It supports a wider range of authentication methods, including biometrics, which allows for quicker and more convenient verification without compromising security.
Q5: Is Multi-factor Authentication (MFA) required for all transactions?
The requirement for MFA can vary depending on the payment gateway, the type of transaction, and regulatory requirements. However, for enhanced security, it’s advisable to use MFA for transactions whenever possible, especially for those involving large amounts of sensitive information.
Q6: What role does artificial intelligence play in fraud monitoring systems?
Artificial intelligence (AI) and machine learning algorithms in fraud monitoring systems analyze transaction data in real time to identify patterns that may indicate fraudulent activity. The ability of AI to learn from each transaction and adapt to new fraud tactics enhances the effectiveness of these systems in detecting and preventing fraud.
Use ReliaBills to Add Another Layer of Security to Your Payment Processing
Today’s business landscape demands robust security measures to ensure safe and secure payment processing. While payment gateways provide essential security features, it’s always a good idea to add an extra layer of protection through the use of a reliable and secure invoicing and payment system like ReliaBills. With ReliaBills, you get both robust security features and seamless payment processing, allowing you to focus on growing your business with peace of mind.
ReliaBills is a cloud-based invoicing and billing software designed to automate payment processes, reduce administrative overhead, and streamline payment processing duties. ReliaBills’ payment processing features include automated recurring billing, payment tracking, payment reminders, online payment processing, and much more!
It also provides valuable tools that help manage customer information, monitor payment records, and create proper billing and collection reports. As a result, invoice and billing management are simple and convenient. You also get access to active customer support, ready to assist you whenever you need help.
Get started with ReliaBills for free today! And if you want more features, you can upgrade your account to ReliaBills PLUS for only $24.95 monthly! Subscribing to ReliaBills PLUS will give you access to advanced features such as automatic payment recovery, SMS notifications, custom invoice creation, advanced reporting, and more!
With ReliaBills, you have an all-in-one solution to your invoicing and payment processing needs. Our convenient solutions will enable you to focus more on running and growing your business. Get started today!
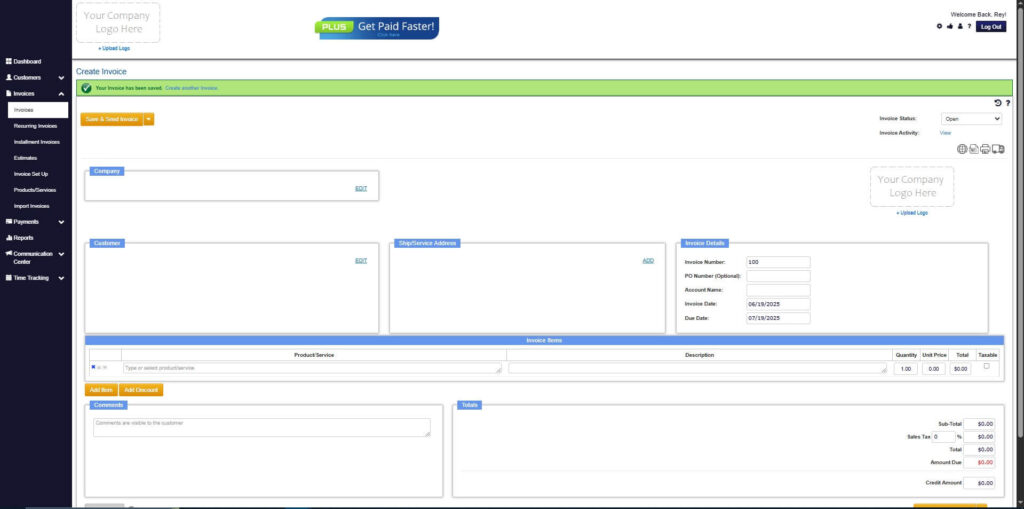
How to Create a New Invoice Using ReliaBills
Creating an invoice using ReliaBills involves the following steps:
Step 1: Login to ReliaBills
- Access your ReliaBills Account using your login credentials. If you don’t have an account, sign up here.
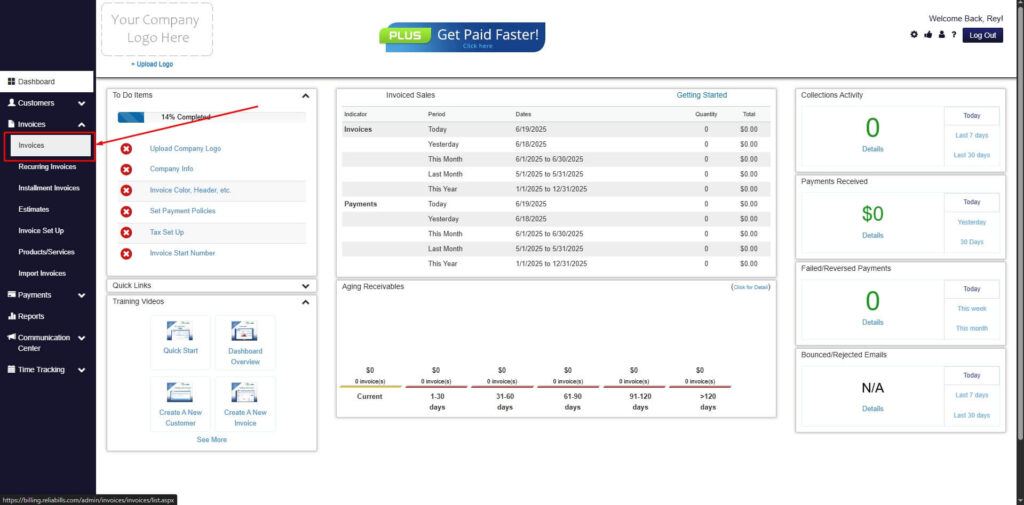
Step 2: Click on Invoices
- Navigate to the Invoices Dropdown and click on Invoices.
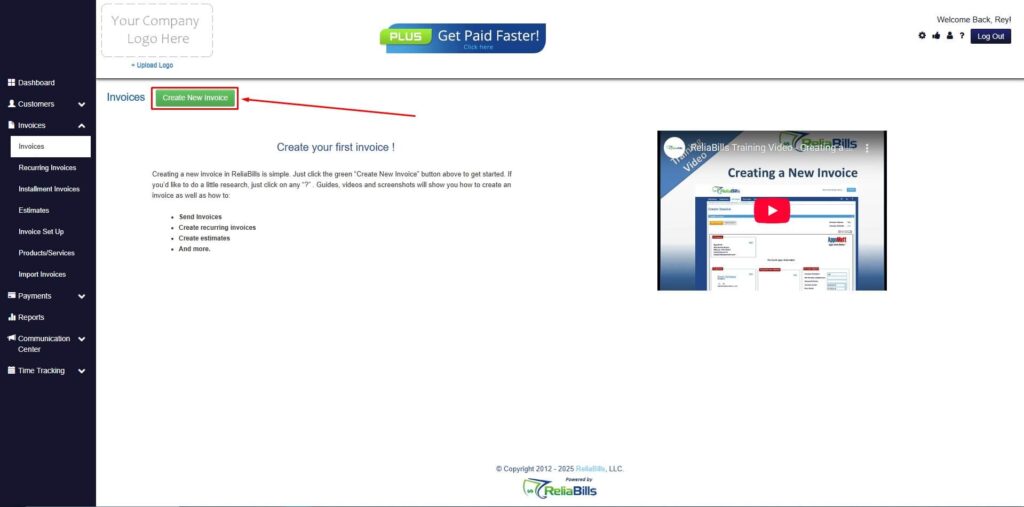
Step 3: Click ‘Create New Invoice’
- Click ‘Create New Invoice’ to proceed.
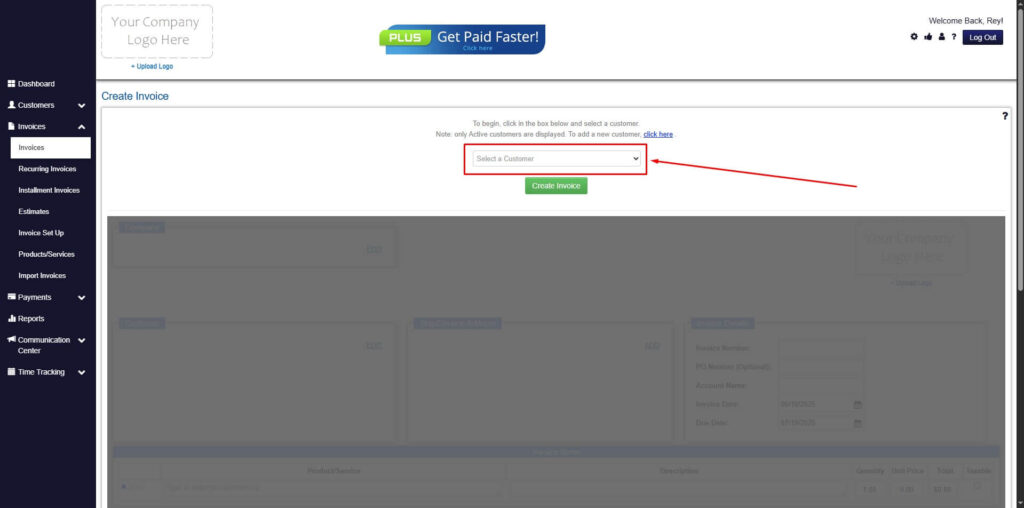
Step 4: Go to the ‘Customers Tab’
- If you have already created a customer, search for them in the Customers tab and make sure their status is “Active”.
Step 5: Create Customer
- If you haven’t created any customers yet, click the ‘Click here’ to create a new customer.
- Provide the First Name, Last Name, and Email to proceed.
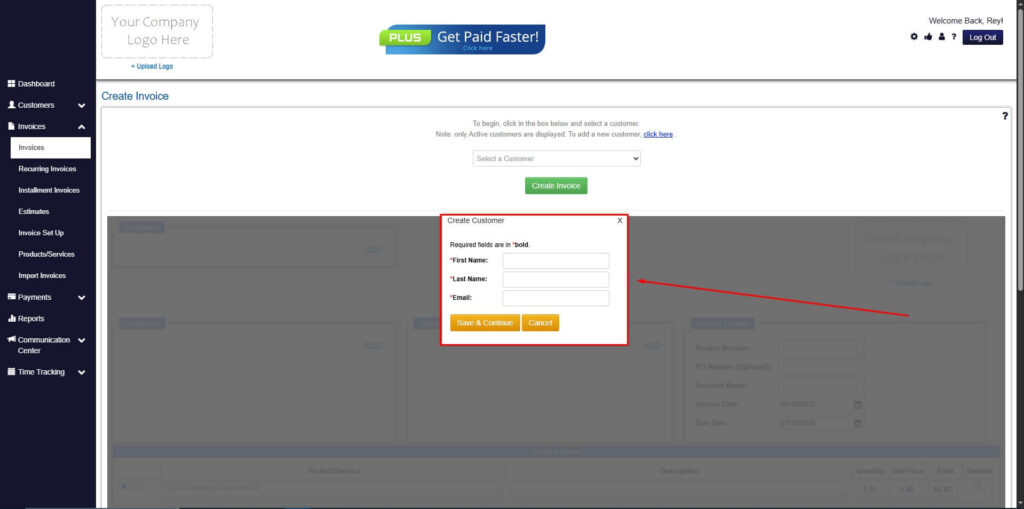
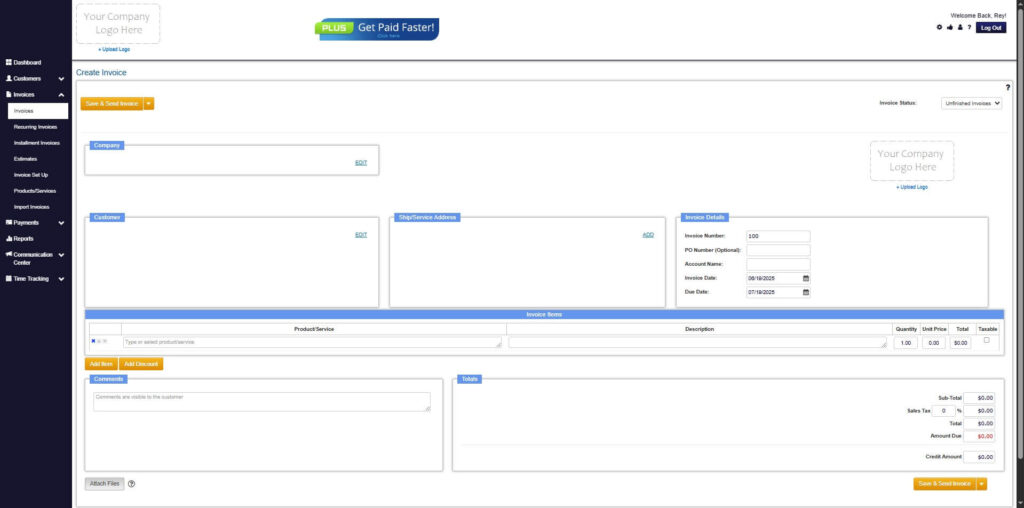
Step 6: Fill in the Create Invoice Form
- Fill in all the necessary fields.
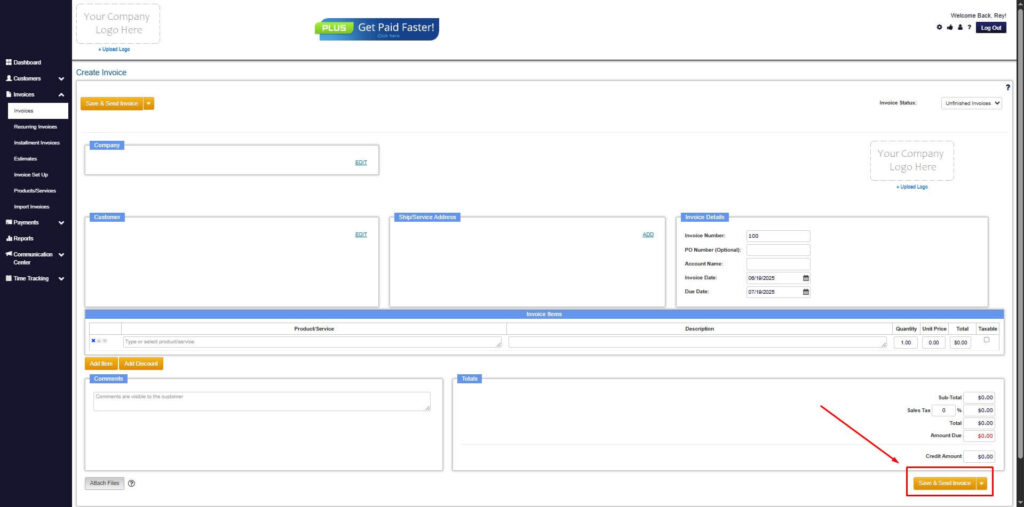
Step 7: Save Invoice
- After filling out the form, click “Save & Send Invoice” to continue.
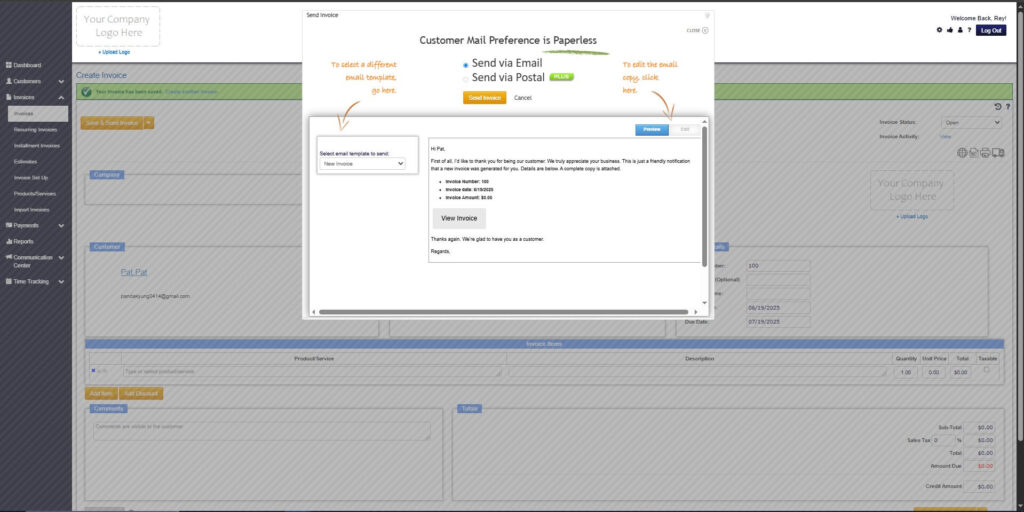
Step 8: Invoice Created
- Your Invoice has been created.
Conclusion
Every lucrative opportunity will always have fraudsters trying to exploit it, and the payment processing industry is no exception. However, with the right mix of technology, awareness, and proactive measures, businesses can significantly mitigate these risks. By utilizing the potential of payment gateways, businesses can ensure a secure and seamless payment processing experience for their customers. Let’s work together to protect our digital ecosystem from cyber threats and build trust with our customers. Remember, a secure business is a successful business! So stay vigilant, stay informed, and keep your payment processing secure.

